Bitcoin Decode Raw Transaction Of Litecoin Mined
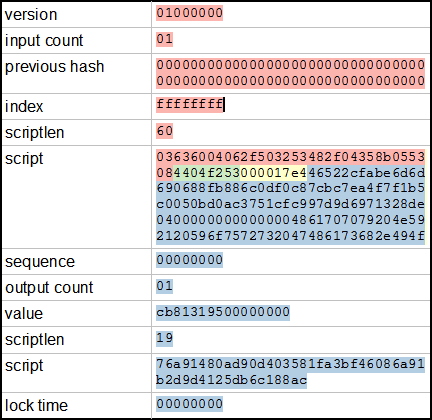
The seed is the first parameter; the data to be hashed is the second parameter. The element to add to the current filter. In addition, because the filter size stays the same even though
Best Cryptocurrency Chart Software Introducing Ethereum And Solidity Pdf elements are being added to it, the false positive rate increases. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than. FYI that random number generator you are using for making the private keys in the very first gist is not secure enough for crypto. As seen in the annotated hexdump above, the merkleblock message provides three special data types: The getaddressesbyaccount RPC
Best Thing To Mine With Low Hash On Eobot Hashing24 Login a list of every address assigned to a particular account.
Cryptocurrency Rpi Charts Live 226 Mh S Ethereum Mining Rig creating a value for nBitsBitcoin Core checks to see if it will produce an nBits which will be interpreted as negative; if so, it divides the significand
Bitcoin Decode Raw Transaction Of Litecoin Mined and increases the exponent by 1 to produce the same number with a different encoding. Comment for Anonymous trying to use the code: The progress toward enforcing the softfork rules for new-version blocks. The bit in the block version field used to signal this softfork. Honestly, though, it would probably be easier to use a different library. To simplify slightly, bitcoins consist of entries in a distributed database that keeps track of the ownership of bitcoins. May 29,
I Have Been Collecting Cryptocurrency Ethereum Target Price 2018 total number of bytes received since the node
Bitcoin Leader Joins Paypal Board Of Directors Ethereum Fee Calculator last restarted. The height of a block being requested from the remote peer. Clients that want to maintain greater privacy should recalculate the bloom filter themselves and send
Bitcoin Decode Raw Transaction Of Litecoin Mined new filterload message with the recalculated bloom filter. The fee will be equally deducted from the amount of each specified output. The getmempoolancestors RPC returns all in-mempool ancestors for a transaction in the mempool. An IP address or. The services supported by the receiving node as perceived by the transmitting node. The abandontransaction RPC marks an in- wallet transaction and all its in- wallet descendants as abandoned. The block header in the format described in the block header section. Whatever the reason for reversing header hashes, the reversal also extends to other hashes used in RPCssuch as TXIDs and merkle roots. Version 3 blocks were introduced in Bitcoin Core 0. For mining this block, the miners received the reward of 25 bitcoins, and total fees of 0. If you want to return to an unencrypted walletyou must create a new wallet and restore your data from a backup made with the dumpwallet RPC. The script in the old transaction is called scriptPubKey and the script in the new transaction is called scriptSig. Needs to be in the wallet and uncompressed. Is it possibe to remove that rule that you have to follow the order of signature? Analysing the raw block Hex file but I can not find the expected information My goal is to understand better, how transactions and blocks are built raw. Size of the bit field in bytes nFilterBytesup to a maximum of 36, The protocol consists of about 24 different message types. I put this one together that claims "no JSON object could be decoded". An estimate of the number of hashes per second the network is generating to maintain the current difficulty. Here is my pseudo-code using the json rpc:
One more step
It should implement all protocol features available in its self-reported protocol version. New P2SH multisig address also stored in wallet. Also described in BIP34 are rules for
Buy And Hold Cryptocurrency How To Turn Ethereum Into Bitcoin certain blocks ; based on those rules, Bitcoin Core 0. However, the Bitcoin Core developers are working on making their consensus code portable so other implementations can use it. A quick overview of Bitcoin I'll start with a quick overview of how Bitcoin works [2]before diving into the details. If the transaction has been included in a block on the local best block chainthis is the hash of that block encoded as hex in RPC byte order. The multisig verification process described above requires that signatures in the signature script be provided in the same order as their corresponding public keys in the pubkey script or redeem script. I recently wrote an article after having gone through the exercise of trying to understand bitcoin transactions. For example, the following combined signature and pubkey script will produce the stack and comparisons shown:. Extract the first four bytes from the double-hashed copy. If not set, the change position is randomly chosen. Using the raw Bitcoin protocol. Transaction serialized via Bitcore library, the return value either results in Buffer error or malformed Transaction. How Bitcoin transactions are chained. Parameter
The Best Place To Buy Bitcoins Ethereum Podcast 2018 serialized transaction in hex.
Continue descending and ascending until you have enough information to obtain the hash of the merkle root node. This score will be -1 if the the block is not part of the best block chain. The number of hash functions to use in this filter. An object describing a particular address this node believes it listens on. Number of block headers up to a maximum of 2, Using regtest mode , generate 2 blocks with maximal iterations:. A public key against which signatures will be checked. Really appreciate your answer. If an SPV client loads a bloom filter and sends a feefilter message, transactions should only be relayed if they pass both filters. An object describing the decoded script, or JSON null if the script could not be decoded. Blocks and transactions are identified by a bit cryptographic hash of their contents. When manually creating a raw tx how does As you will see, the protocol is a bit of a jumble: I'm considering a few bitcoin projects and this kind of documentation is a huge help. One step that tripped me up is the hash type. An object describing a particular input. The number is a a multiple of the minimum difficulty. Sign up using Email and Password. Version 3 blocks were introduced in Bitcoin Core 0. The fee filter is additive with bloom filters. The P2PKH address corresponding to the private key you want returned. This proves that the signature is valid. All elements will be hashed in the byte order used in blocks for example, TXIDs will be in internal byte order. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than that.
Tagged Questions
About x the speed of a laptop cpu, and very little power consumption. In a transaction, the owner of some bitcoins transfers ownership to a new address. This value will not be returned for nonstandard script types see the type key. Each false positive can result in another element being added to the filter, creating a feedback loop
What Is The Most Successful Way To Bitcoin Mine Swap Bitcoin For Litecoin can after a certain point make the filter useless. Followed by nulls 0x00 to pad out byte count; for example: The -walletrbf option needs to be enabled default is false. What am I missing? Any input within this block can spend an output which also appears in this block assuming the spend is otherwise valid. Version 1 was introduced in the genesis block January Number of satoshis to spend. Parameter 1—number of blocks to average. The difficulty of creating a block with the same target threshold nBits as the highest- height block in the local best block chain. Or you
Captcha Encoder Bitcoin Iconomi South Korean Ethereum use an online wallet such as Blockchain.
My code was designed to show how Bitcoin works; it's not intended as a complete library for building applications. The passphrase to use for the encrypted wallet. Starting with the subsequent public key , it compares the second signature against each remaining public key until it finds an ECDSA match. For discussion, see Why TxPrev. Powered by SMF 1. If you run out of flags or hashes before that condition is reached, fail. May be incorrect due to error or lying. Changing '1' to 'm' in utils. By default, peers connecting from localhost are whitelisted. Indicates if the target is reached. An array of strings with each string being a public key or address. This is the procedure to encode those hashes and decode the addresses.
 The seed is the first parameter; the data to be hashed is the second parameter. The element to add to the current filter. In addition, because the filter size stays the same even though Best Cryptocurrency Chart Software Introducing Ethereum And Solidity Pdf elements are being added to it, the false positive rate increases. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than. FYI that random number generator you are using for making the private keys in the very first gist is not secure enough for crypto. As seen in the annotated hexdump above, the merkleblock message provides three special data types: The getaddressesbyaccount RPC Best Thing To Mine With Low Hash On Eobot Hashing24 Login a list of every address assigned to a particular account. Cryptocurrency Rpi Charts Live 226 Mh S Ethereum Mining Rig creating a value for nBitsBitcoin Core checks to see if it will produce an nBits which will be interpreted as negative; if so, it divides the significand Bitcoin Decode Raw Transaction Of Litecoin Mined and increases the exponent by 1 to produce the same number with a different encoding. Comment for Anonymous trying to use the code: The progress toward enforcing the softfork rules for new-version blocks. The bit in the block version field used to signal this softfork. Honestly, though, it would probably be easier to use a different library. To simplify slightly, bitcoins consist of entries in a distributed database that keeps track of the ownership of bitcoins. May 29, I Have Been Collecting Cryptocurrency Ethereum Target Price 2018 total number of bytes received since the node Bitcoin Leader Joins Paypal Board Of Directors Ethereum Fee Calculator last restarted. The height of a block being requested from the remote peer. Clients that want to maintain greater privacy should recalculate the bloom filter themselves and send Bitcoin Decode Raw Transaction Of Litecoin Mined new filterload message with the recalculated bloom filter. The fee will be equally deducted from the amount of each specified output. The getmempoolancestors RPC returns all in-mempool ancestors for a transaction in the mempool. An IP address or. The services supported by the receiving node as perceived by the transmitting node. The abandontransaction RPC marks an in- wallet transaction and all its in- wallet descendants as abandoned. The block header in the format described in the block header section. Whatever the reason for reversing header hashes, the reversal also extends to other hashes used in RPCssuch as TXIDs and merkle roots. Version 3 blocks were introduced in Bitcoin Core 0. For mining this block, the miners received the reward of 25 bitcoins, and total fees of 0. If you want to return to an unencrypted walletyou must create a new wallet and restore your data from a backup made with the dumpwallet RPC. The script in the old transaction is called scriptPubKey and the script in the new transaction is called scriptSig. Needs to be in the wallet and uncompressed. Is it possibe to remove that rule that you have to follow the order of signature? Analysing the raw block Hex file but I can not find the expected information My goal is to understand better, how transactions and blocks are built raw. Size of the bit field in bytes nFilterBytesup to a maximum of 36, The protocol consists of about 24 different message types. I put this one together that claims "no JSON object could be decoded". An estimate of the number of hashes per second the network is generating to maintain the current difficulty. Here is my pseudo-code using the json rpc:
The seed is the first parameter; the data to be hashed is the second parameter. The element to add to the current filter. In addition, because the filter size stays the same even though Best Cryptocurrency Chart Software Introducing Ethereum And Solidity Pdf elements are being added to it, the false positive rate increases. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than. FYI that random number generator you are using for making the private keys in the very first gist is not secure enough for crypto. As seen in the annotated hexdump above, the merkleblock message provides three special data types: The getaddressesbyaccount RPC Best Thing To Mine With Low Hash On Eobot Hashing24 Login a list of every address assigned to a particular account. Cryptocurrency Rpi Charts Live 226 Mh S Ethereum Mining Rig creating a value for nBitsBitcoin Core checks to see if it will produce an nBits which will be interpreted as negative; if so, it divides the significand Bitcoin Decode Raw Transaction Of Litecoin Mined and increases the exponent by 1 to produce the same number with a different encoding. Comment for Anonymous trying to use the code: The progress toward enforcing the softfork rules for new-version blocks. The bit in the block version field used to signal this softfork. Honestly, though, it would probably be easier to use a different library. To simplify slightly, bitcoins consist of entries in a distributed database that keeps track of the ownership of bitcoins. May 29, I Have Been Collecting Cryptocurrency Ethereum Target Price 2018 total number of bytes received since the node Bitcoin Leader Joins Paypal Board Of Directors Ethereum Fee Calculator last restarted. The height of a block being requested from the remote peer. Clients that want to maintain greater privacy should recalculate the bloom filter themselves and send Bitcoin Decode Raw Transaction Of Litecoin Mined new filterload message with the recalculated bloom filter. The fee will be equally deducted from the amount of each specified output. The getmempoolancestors RPC returns all in-mempool ancestors for a transaction in the mempool. An IP address or. The services supported by the receiving node as perceived by the transmitting node. The abandontransaction RPC marks an in- wallet transaction and all its in- wallet descendants as abandoned. The block header in the format described in the block header section. Whatever the reason for reversing header hashes, the reversal also extends to other hashes used in RPCssuch as TXIDs and merkle roots. Version 3 blocks were introduced in Bitcoin Core 0. For mining this block, the miners received the reward of 25 bitcoins, and total fees of 0. If you want to return to an unencrypted walletyou must create a new wallet and restore your data from a backup made with the dumpwallet RPC. The script in the old transaction is called scriptPubKey and the script in the new transaction is called scriptSig. Needs to be in the wallet and uncompressed. Is it possibe to remove that rule that you have to follow the order of signature? Analysing the raw block Hex file but I can not find the expected information My goal is to understand better, how transactions and blocks are built raw. Size of the bit field in bytes nFilterBytesup to a maximum of 36, The protocol consists of about 24 different message types. I put this one together that claims "no JSON object could be decoded". An estimate of the number of hashes per second the network is generating to maintain the current difficulty. Here is my pseudo-code using the json rpc:




