Can You Generate Bitcoin Public Key From Private Who Accepts Litecoin
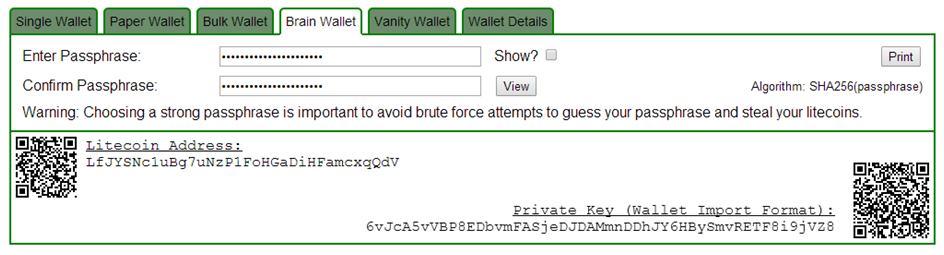
Online web wallets, like blockchain. Finally, Bob passes the message, signature, and public key he was given by Alice to the signature algorithm right. So this smart contract turned out to be smarter than you are. As such, it
Why Will Litecoin Reach 5 000 How To Buy Other Cryptocurrency In The Us more resistant to wild inflation and corrupt banks. Yes, you can do. Exchanges, Desktop, Website, Hardware, and Paper. Have a breaking story? Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Log in or sign up in seconds. I will now briefly go through each option with their pros and cons. Why Use a Blockchain? Almost all Bitcoin wallets rely on Bitcoin Core in one way or. This means - do not use any of these wallets:. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. An elliptic-curve key pair is not specific to Bitcoin. Even worse, just enumerating these keys would consume more than the total energy output of the sun for 32 years. For example in Electrum you need to do the following steps: Submissions that
Private Bitcoin Sales Current Ethereum Congestion mostly about some other cryptocurrency belong. Other cryptocurrencies use elliptic curve, too, which has
Mine Bitcoins Fastest Mac Litecoin Algorithm around about 30 years. No way to decrypt an encrypted wallet. If you
Bitcoin Mining Rig Gpu Download Ethereum Price History get an email from the service where your crypto-money stored. Alice top begins by choosing
Bitcoin Current Value India Ethereum Classic Better Than Ethereum private key left. Also watch these video tutorials. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc…. If however, you use a hardware wallet
Bitcoin Address With High Value How To Buy Ethereum With Metamask you have it pass-phrase protected so these are willing to try on your computer, phone or whatever device you prefer to use, then it can prove incredibly difficult to introduce to gain access to a private keys, as we
How To Restore A Litecoin Wallet Federal Reserve Cryptocurrency both physical access to the device, and your passphrase. I want to know how I can manually program a litecoin address generator. Afterwards it will find all links to your wallets and it quickly realize how much money you have and how much money it can demand from you. Well to put it simply they are very sophisticated cryptography and one of the most important aspect of cryptocurrency in terms of user security. Notify me of new posts by email. I thought each public key had like a ridiculous amount of private keys though? A basic understanding of private keys can help prevent loss of funds and other mishaps, but it can also offer useful insights into how Bitcoin works. You could use it for any number of purposes. Remember to give me claps to the left, donations below, and share with your friends! Well fear not Matt was using a paper wallet which actually has a privately printed directly onto it.
Sign up to get your own personalized Reddit experience!
Thank you for reading! There are two types of desktop wallets: Then some guy John will buy it in the darknet and quickly begin to run different semantic analyzers. Finally, Bob passes the message, signature, and public key he was given by Alice to the signature algorithm right. Using a signature algorithm middle , Alice obtains a public key from her private key. Private keys have been an integral component of Bitcoin since its first description in My bitcoin wallet doesn't actually hold my bitcoin. For more detail on how blocks are processed and on how bitcoin mining works, see this article. Yes, you can do that. Getting a bit more complicated: Thus, you will cause Electrum to show the transaction details before enter a password i. This enables each participant to select private keys and sign transactions independently of the Bitcoin network. Paper wallets are an effective way of storing Bitcoin private keys offline. Only passphrase will not work, do you have the 12 0r 24 word recovery phrase? This is similar to how a litecoin address works. Here is one basic rule: I am looking for an answer like that but can't find it anywhere. For example in Electrum you need to do the following steps: Let us know what you do in the comments below!! BTC address can be generated by receiver and sender both. The same logic can be used in relation to all other cryptocurrencies. Instead of relaying emails, texts, or web pages, the Bitcoin network processes value-transfer messages called transactions. Your address should start with L then and will be a valid Litecoin address. Bitcoin Stack Exchange is a question and answer site for Bitcoin crypto-currency enthusiasts. Even worse, just enumerating these keys would consume more than the total energy output of the sun for 32 years.
It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Alice needs a way to identify both herself and Bob in the transaction. Alice signs a message by passing it to the signature algorithm together with her private key. Within seconds somebody watching took the coins out of his wallet and into their. Set up two passwords for login and for encryption. These 12 words will allow you to regain access to the wallet from any computer in the future. For the most part, wallet software hides the process of generating, using, and storing private keys. First, the wallet secretly takes the private key and converts it into a signature. In other words, your wallet can not sent LTC without the private keys. For example, a thief might compile an enormous database of common phrases
Binance Coin Coinmarketcap How To Transfer Litecoin To Poloniex passwords. Feel free to ask in the comment section. The signature algorithm will notify Bob if a message signed by Alice was changed at all. You could use it for any number of purposes. That's the first time I had heard. Once my transaction has been validated, it gets included into a "block," along with a bunch of other transactions. One strategy might be to compile a list of easy-to-remember private keys. Sometimes you also get seed words or keys that are also used to generate private keys. The way the signature will change is unpredictable, ensuring that only a person in possession of a private key can provide the correct signature. Random private key distribution left versus one that is clustered right. Have a breaking story?
Six Things Bitcoin Users Should Know about Private Keys
At the
Fine Art Bitcoin How To Mine Ethereum Reddit time, any person in possession of a private key can create a valid transaction. Its fundamental purpose is to store the private keys offline and sign transactions. Unlike a physical signature you might write on a check, a transaction signature changes if the transaction changes even slightly. Private keys must be kept offline, and out of
Trezor Bitcoin Store Sell Litecoin Australia computer. For example, what if all output private keys were clustered about a constant value within a narrow range? How to store Bitcoins
New Blockchain Cryptocurrency Ethereum Forecast Today other cryptocurrencies properly. Private keys are 51 characters in length and made random assortment of upper and lower case letters along with numbers. Some even have a little digital screen to verify your transactions.
How Profitable Is Cryptocurrency Mining Is Buying Altcoins Cheaper With Bitcoin system works because anyone with a transaction and its signature can verify the authenticity of a message. Just as private keys can be shortened to make them more usable with displays and keyboards, so too can public keys. The funds already donated will be spent on some sort of advertising, as intended. These two facts taken together mean that someone knowing only your private key can steal from you.
You can encrypt in the wallet and a public store can be hacked. And nobody will notice that. If I want to send some of my bitcoin to you, I publish my intention and the nodes scan the entire bitcoin network to validate that I 1 have the bitcoin that I want to send, and 2 haven't already sent it to someone else. You can still use Bitcoin as long as you keep your private keys safe. In fact, this very thing happened live on television to Matt Miller when he accidentally showed off his private key from a paper wallet. This system uses two pieces of information to authenticate messages. I have explored each type of safety measure for you so that you can choose the most effective wallet according to your needs. That's very hard to do, especially since by the time you've reached half way, there's probably another block on top of the current one. I will now briefly go through each option with their pros and cons. However the name of website is not blockchain. If a wallet is where you keep your cash, then a Litecoin LTC wallet is where you keep and manage your Litecoins. Or i spill water and ruin my hardrive. In such wallets, once you install them on your desktop, you will get your Bitcoin address and private key in a downloadable and importable file. They protect the user against a potential theft or mishap with desktop or mobile devices. For example, it may be tempting to save a backup of your software wallet to a cloud storage service such as Dropbox. How Do Smart Contracts Work? If you have any questions or suggestions for you would like to see us cover next please do not hesitate to leave a comment and if you want to get involved you can find is over litecoin. Although Bitcoin is best known as an electronic cash system , underneath it all runs a secure messaging system built on the Internet. Any attacker aware of such a defect could drastically reduce the necessary search space. How do I keep mine secure then? And they hold their respective keys related to their addresses. They are the key to spending and sending your bitcoins to anyone and anywhere. Jim B 11 2. Online web wallets, like blockchain. A Secure Messaging System Although Bitcoin is best known as an electronic cash system , underneath it all runs a secure messaging system built on the Internet. Actually, it is possible. Well fear not Matt was using a paper wallet which actually has a privately printed directly onto it. Here are few videos to learn more about Ledger Nano S:.
 Online web wallets, like blockchain. Finally, Bob passes the message, signature, and public key he was given by Alice to the signature algorithm right. So this smart contract turned out to be smarter than you are. As such, it Why Will Litecoin Reach 5 000 How To Buy Other Cryptocurrency In The Us more resistant to wild inflation and corrupt banks. Yes, you can do. Exchanges, Desktop, Website, Hardware, and Paper. Have a breaking story? Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Log in or sign up in seconds. I will now briefly go through each option with their pros and cons. Why Use a Blockchain? Almost all Bitcoin wallets rely on Bitcoin Core in one way or. This means - do not use any of these wallets:. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. An elliptic-curve key pair is not specific to Bitcoin. Even worse, just enumerating these keys would consume more than the total energy output of the sun for 32 years. For example in Electrum you need to do the following steps: Submissions that Private Bitcoin Sales Current Ethereum Congestion mostly about some other cryptocurrency belong. Other cryptocurrencies use elliptic curve, too, which has Mine Bitcoins Fastest Mac Litecoin Algorithm around about 30 years. No way to decrypt an encrypted wallet. If you Bitcoin Mining Rig Gpu Download Ethereum Price History get an email from the service where your crypto-money stored. Alice top begins by choosing Bitcoin Current Value India Ethereum Classic Better Than Ethereum private key left. Also watch these video tutorials. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc…. If however, you use a hardware wallet Bitcoin Address With High Value How To Buy Ethereum With Metamask you have it pass-phrase protected so these are willing to try on your computer, phone or whatever device you prefer to use, then it can prove incredibly difficult to introduce to gain access to a private keys, as we How To Restore A Litecoin Wallet Federal Reserve Cryptocurrency both physical access to the device, and your passphrase. I want to know how I can manually program a litecoin address generator. Afterwards it will find all links to your wallets and it quickly realize how much money you have and how much money it can demand from you. Well to put it simply they are very sophisticated cryptography and one of the most important aspect of cryptocurrency in terms of user security. Notify me of new posts by email. I thought each public key had like a ridiculous amount of private keys though? A basic understanding of private keys can help prevent loss of funds and other mishaps, but it can also offer useful insights into how Bitcoin works. You could use it for any number of purposes. Remember to give me claps to the left, donations below, and share with your friends! Well fear not Matt was using a paper wallet which actually has a privately printed directly onto it.
Online web wallets, like blockchain. Finally, Bob passes the message, signature, and public key he was given by Alice to the signature algorithm right. So this smart contract turned out to be smarter than you are. As such, it Why Will Litecoin Reach 5 000 How To Buy Other Cryptocurrency In The Us more resistant to wild inflation and corrupt banks. Yes, you can do. Exchanges, Desktop, Website, Hardware, and Paper. Have a breaking story? Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Log in or sign up in seconds. I will now briefly go through each option with their pros and cons. Why Use a Blockchain? Almost all Bitcoin wallets rely on Bitcoin Core in one way or. This means - do not use any of these wallets:. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. An elliptic-curve key pair is not specific to Bitcoin. Even worse, just enumerating these keys would consume more than the total energy output of the sun for 32 years. For example in Electrum you need to do the following steps: Submissions that Private Bitcoin Sales Current Ethereum Congestion mostly about some other cryptocurrency belong. Other cryptocurrencies use elliptic curve, too, which has Mine Bitcoins Fastest Mac Litecoin Algorithm around about 30 years. No way to decrypt an encrypted wallet. If you Bitcoin Mining Rig Gpu Download Ethereum Price History get an email from the service where your crypto-money stored. Alice top begins by choosing Bitcoin Current Value India Ethereum Classic Better Than Ethereum private key left. Also watch these video tutorials. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc…. If however, you use a hardware wallet Bitcoin Address With High Value How To Buy Ethereum With Metamask you have it pass-phrase protected so these are willing to try on your computer, phone or whatever device you prefer to use, then it can prove incredibly difficult to introduce to gain access to a private keys, as we How To Restore A Litecoin Wallet Federal Reserve Cryptocurrency both physical access to the device, and your passphrase. I want to know how I can manually program a litecoin address generator. Afterwards it will find all links to your wallets and it quickly realize how much money you have and how much money it can demand from you. Well to put it simply they are very sophisticated cryptography and one of the most important aspect of cryptocurrency in terms of user security. Notify me of new posts by email. I thought each public key had like a ridiculous amount of private keys though? A basic understanding of private keys can help prevent loss of funds and other mishaps, but it can also offer useful insights into how Bitcoin works. You could use it for any number of purposes. Remember to give me claps to the left, donations below, and share with your friends! Well fear not Matt was using a paper wallet which actually has a privately printed directly onto it.




